The Growing Digital Threat Landscape: Why Online Security is a Non-Negotiable Skill
The digital age has transformed nearly every aspect of our lives. From online banking to remote work and even controlling smart devices in our homes, our dependence on technology grows deeper every day. But this convenience comes with a price: an ever-evolving digital threat landscape that makes cybersecurity awareness and online security skills non-negotiable. Cybercrime has evolved from occasional disruptions into a multi-trillion-dollar global industry, driven by highly skilled hackers, automated attack tools, and advanced social engineering scams. What was once a rare inconvenience has now become a constant and dangerous risk for both individuals and businesses.
- Cybersecurity Awareness Is Essential in the Digital Age – As our dependence on online banking, remote work, and smart devices grows, the digital threat landscape expands, making cybersecurity and online security skills a non-negotiable life skill.
- Individuals Are Prime Targets for Cybercrime – Hackers no longer focus only on corporations; they exploit individuals through weak security practices, with every connected device or account serving as a potential entry point for cyberattacks.
Understanding the fundamentals of digital protection strategies is the first and most effective line of defense. Today, hackers are not just targeting corporations—they are actively exploiting individuals who lack strong online security practices. Every connected account and device represents an entry point for attackers. Without the right knowledge and preventive measures, you could unknowingly leave your most sensitive information exposed.

How Cybercriminals Exploit Everyday Digital Habits
Think about how much of your life exists online. Your banking information, medical records, tax filings, personal photos, and even smart home devices are stored and transmitted digitally. A single vulnerability—such as a weak password, outdated software, or falling for a phishing email—can provide cybercriminals with access to this treasure trove of personal data.
- Vast Digital Footprint: A significant portion of our lives, including banking, medical, and personal data, exists online, making it highly susceptible to cyber threats from a single vulnerability.
- Sophisticated and Evolving Threats: Modern cyberattacks are advanced and diverse, moving beyond simple spam to include AI-powered phishing and ransomware. These attacks exploit human vulnerabilities to cause devastating financial and personal consequences.
Modern threats extend far beyond spam emails. Cybercriminals use advanced methods like ransomware attacks, credential stuffing, identity theft schemes, and AI-powered phishing campaigns. These attacks are carefully designed to exploit human nature, whether it’s curiosity, trust, or urgency. For example, a phishing message disguised as a legitimate bank alert can trick someone into revealing their login credentials within seconds. The consequences can be devastating: drained accounts, stolen identities, and emotional distress that may take years to overcome.

The Financial and Emotional Cost of Cybercrime
Cybercrime is not just a digital nuisance—it is both a financial and personal crisis. For individuals, a single successful breach can result in financial loss, identity theft, damaged credit scores, and emotional trauma. Recovering from cybercrime can take years, involving legal battles, expensive credit monitoring services, and countless hours spent repairing damage.
- Cybercrime is a Dual Crisis: For both individuals and businesses, cybercrime represents a profound financial and personal crisis. Individuals face potential identity theft, financial ruin, and emotional distress, while businesses risk millions in losses, regulatory fines, and irreparable damage to their reputation and customer trust.
- Proactive Investment is Essential: Cybersecurity is no longer an optional expense but a critical investment. For businesses, implementing training, proactive threat detection, and data protection strategies is a necessary measure to prevent devastating attacks and ensure long-term stability and customer loyalty.
For businesses, the stakes are even higher. A single data breach can cost millions, not only in recovery expenses and regulatory fines but also in terms of lost customer trust and long-term reputational damage. In fact, many small and medium-sized businesses never fully recover after a major cyberattack. That’s why cybersecurity training, proactive threat detection, and data protection strategies have become essential investments rather than optional expenses.
Expanding Attack Surfaces in a Connected World
The rise of remote work, cloud computing, and the Internet of Things (IoT) has drastically expanded the attack surface available to hackers. Every new smart device—whether it’s a connected thermostat, doorbell camera, or refrigerator—introduces another potential entry point for cybercriminals. If not properly secured, these devices can serve as weak links in your personal or business network.
- Expanded Attack Surface: The shift to remote work, cloud computing, and the proliferation of IoT devices has significantly broadened the potential entry points for hackers. Each connected device and personal network introduces a new vulnerability, making it crucial for everyone to understand how to secure these new frontiers.
- Cybersecurity as a Foundational Life Skill: The blurring of professional and personal digital lives means that cybersecurity is no longer a niche concern for IT professionals. Protecting against modern threats—which exploit human vulnerabilities on personal devices and home networks—has become a fundamental life skill that everyone must learn to safeguard their data.
This blurred line between professional and personal life creates more vulnerabilities. Remote employees accessing sensitive company data from insecure home networks, or families leaving their IoT devices unprotected, significantly increase the risks. In today’s world, understanding cybersecurity best practices is no longer just a responsibility for IT professionals—it’s a life skill that everyone needs.

Cybersecurity as a Digital Life Skill
To better understand this, imagine living in a world where everyone keeps their valuables in clear, unlocked boxes on their front lawn. While some people might leave your belongings untouched, opportunistic criminals would inevitably seize the chance to take what they want. The internet functions in much the same way. Without protection, your most valuable digital assets are exposed to anyone who knows how to look.
- The Digital World is an “Unlocked Front Lawn”: The analogy of leaving valuables in clear, unlocked boxes on a front lawn effectively illustrates our vulnerability in the digital world. Without proper cybersecurity measures, our most valuable digital assets are exposed and ripe for exploitation by opportunistic cybercriminals.
- Cybersecurity is an Essential “Digital Vault”: To counteract this vulnerability, cybersecurity provides a necessary “digital vault.” Essential safeguards like strong passwords, two-factor authentication, and awareness of phishing are not optional; they are fundamental practices for protecting your digital life, just as you would protect your physical home with locks and security measures.
Cybersecurity is the digital vault that keeps your assets safe. Strong passwords, two-factor authentication, regular software updates, and awareness of phishing techniques are not optional extras—they are essential safeguards. Just as you wouldn’t leave your home unlocked at night, you should never leave your digital life unprotected.
Common Cyber Threats: How to Spot a Phishing Scam and Avoid Malware
One of the most valuable aspects of learning about cybersecurity is gaining the ability to recognize and respond to common threats. Many successful cyberattacks don’t exploit a technical flaw but rather a human one. Cybercriminals are experts in social engineering—manipulating people into giving up sensitive information. Understanding their tactics is a crucial part of building your personal defense.
Phishing, Spear Phishing, and Smishing: The Art of Digital Deception
Phishing is the most widespread cybercrime, and it’s a perfect example of a threat that relies on a lack of awareness. It’s an attack where an attacker sends a fraudulent message designed to trick a person into revealing sensitive information or deploying malicious software.
- What to look for: A phishing email often creates a false sense of urgency or fear, claiming a problem with your bank account, a pending delivery, or a tax issue. It might also offer a reward or prize that seems too good to be true. The email will contain a link that directs you to a fake website designed to look like a legitimate one. The goal is to trick you into entering your credentials or personal information, which the attacker then steals.
- An example in action: You receive an email that looks like it’s from Amazon, telling you there’s an issue with your recent order and asking you to click a link to “confirm your details.” The email address might be “amazon-support@gmail.com” instead of the official domain. A quick look at the sender’s address reveals the scam, but in a moment of panic, many people click without thinking.
- Be skeptical of unsolicited messages that ask for personal information.
- Always verify the sender’s email address and hover over links to see the true destination before clicking.
Malware: The Digital Pest You Need to Evade
Malware is an umbrella term for malicious software designed to disrupt computer operations, gather sensitive information, or gain unauthorized access. Common types include viruses, spyware, and ransomware. While antivirus software is essential, personal vigilance is the key to preventing the initial infection.
- How it gets on your device: Malware often arrives as an attachment in a phishing email or is hidden within a “free” software download from an untrusted source. Once you click on the malicious link or open the infected file, the software can silently install itself and begin its work. A ransomware attack, for instance, can encrypt all your files, locking you out of your data and demanding a ransom payment.
- An example in action: An unsuspecting user downloads a free copy of a popular video game from a third-party website. Unbeknownst to them, the download is bundled with spyware. The spyware records their keystrokes, capturing usernames and passwords for their bank accounts and other services, which are then sent to the attacker.
- Only download software from official, trusted sources.
- Avoid opening email attachments from unknown senders, especially if they have strange file names.
Actionable Steps: Simple Strategies for Online Security and Personal Data Protection
The good news is that you don’t need to be a cybersecurity expert to make a huge impact on your own safety. A few simple, consistent habits can build a powerful shield against most common threats. Learning about cybersecurity is about empowering yourself with these practical skills.
Mastering Your Passwords: The Foundation of Digital Security
Your passwords are the first and most critical line of defense. A weak or reused password is an open invitation for a cybercriminal.
- Create strong, unique passwords for every account. Use a combination of uppercase and lowercase letters, numbers, and symbols. A phrase like “TacoTuesday!2025” is much stronger than “password123.”
- Use a password manager. These applications are a godsend for cybersecurity. They securely store all your complex, unique passwords, so you only have to remember one master password. They can also auto-generate ultra-strong passwords for you.
- Enable Multi-Factor Authentication (MFA). This is perhaps the most important thing you can do to secure your accounts. MFA requires a second piece of verification beyond your password, like a code sent to your phone or an authenticator app. Even if a criminal steals your password, they can’t log in without the second factor. Most major services, from Google to your bank, offer this feature, and you should enable it on every single one.
How you interact with the internet can be just as important as the security measures you have in place.
- Check for HTTPS. When you’re on a website, especially one where you’re entering personal or financial information, always check that the URL starts with “https://”. The “s” stands for secure and means the data being transferred is encrypted.
- Be cautious with public Wi-Fi. Public networks at coffee shops, airports, and hotels are often unsecured. It is possible for hackers to “eavesdrop” on your data. Avoid conducting sensitive activities like online banking or shopping on these networks. If you must use them, use a Virtual Private Network (VPN) to encrypt your connection. For more insights on this topic, you can read this article about safeguarding your online data from Luqoz.com.
Career Opportunities in Cybersecurity: A Look at a Growing Field
Beyond personal protection, learning about cybersecurity can open up a world of professional opportunities. The demand for skilled cybersecurity professionals is exploding, with a severe shortage of qualified individuals. As businesses and governments face increasingly sophisticated threats, the need for experts to protect their data, networks, and systems has never been greater.
- High demand and excellent job security. According to the U.S. Bureau of Labor Statistics, employment of information security analysts is projected to grow much faster than the average for all occupations. The cybersecurity job market has a near-zero unemployment rate, making it one of the most stable and promising careers in technology.
- Diverse roles and specializations. The field is incredibly varied, with roles that cater to different interests and skill sets. You don’t have to be a coding genius to have a successful career. Roles include:
- Ethical Hacker / Penetration Tester: Professionals who legally hack into systems to find and fix vulnerabilities before criminals do.
- Security Analyst: Individuals who monitor for and respond to security threats.
- Forensics Investigator: Experts who analyze digital evidence to trace cyberattacks and identify perpetrators.
- Risk Management and Compliance Officer: Professionals who ensure an organization adheres to security regulations and policies.
The average salary for a cybersecurity professional is highly competitive, reflecting the immense value and critical nature of the work. For anyone looking for a stable, high-paying, and intellectually stimulating career, exploring cybersecurity career paths is a fantastic option.
FAQs About the Importance of Cybersecurity Education
We’ve covered a lot of ground, but you might still have some specific questions about the importance of digital protection. Here are answers to some of the most common queries.
Is cybersecurity only important for people who work with computers? A: Absolutely not! While professionals in IT and tech fields need a deeper understanding, learning about cybersecurity is important for everyone. We all use computers, smartphones, and the internet for banking, shopping, and communication. These activities expose us to risks that require basic security knowledge to mitigate.
How can I teach my children about cybersecurity? A: Start early with age-appropriate lessons. Teach them to create strong passwords, be careful about what they share online, and never click on links or download files from people they don’t know. Explain the concept of “stranger danger” in the digital world. Emphasize that what they see online isn’t always real and that it’s important to ask for help if something makes them uncomfortable.
Is my home Wi-Fi network secure just because it has a password? A: A password is a good start, but it’s not enough. You should also change the default router name and password, ensure your network uses WPA2 or WPA3 encryption, and regularly update your router’s firmware. Creating a separate guest network for visitors is also a great way to isolate your main devices from potential risks.
What is the most common mistake people make with their cybersecurity? A: The most common mistake is reusing passwords across multiple accounts. This means that if a criminal obtains the password for just one of your accounts (from a data breach, for example), they can potentially access all of your other accounts that use the same password. Using a password manager and unique passwords for every site is the single most effective action you can take to prevent this.
Q1: What is cyber security and why is it important?
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks. It is important because it safeguards personal information, financial assets, and critical infrastructure from cybercriminals.
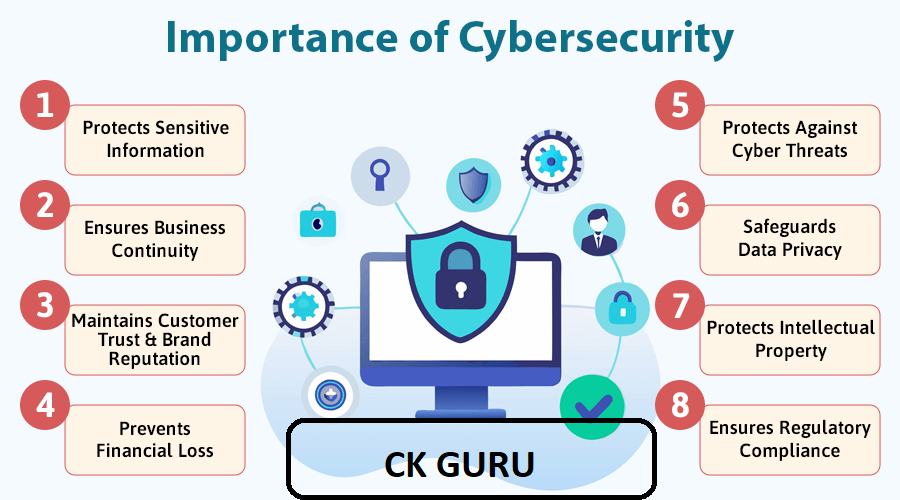
Q2: Which are the 5 reasons cybersecurity is important?
- Protects sensitive data.
- Prevents financial loss.
- Maintains customer trust.
- Reduces risks of cyberattacks.
- Ensures compliance with regulations.
Q3: Why is cyber security education important?
Cybersecurity education helps individuals recognize online threats, avoid scams, and adopt safe digital habits, reducing the chances of falling victim to cybercrime.
Q4: Why is cyber security important to students?
Students are frequent targets of phishing, identity theft, and social media scams. Cybersecurity helps them protect their academic records, financial data, and online reputation.
Q5: What are the benefits of studying cyber security?
Studying cybersecurity opens doors to high-paying careers, provides skills to protect organizations, and equips individuals to fight against global cybercrime.
Q6: What are the 7 types of cyber security?
- Network security
- Cloud security
- Endpoint security
- Application security
- Mobile security
- IoT security
- Operational security
Q7: Who is the father of cyber security?
August Kerckhoffs is often referred to as the “father of cybersecurity” for his early work in information security principles.
Q8: What is the main purpose of cyber security?
The main purpose is to protect data, ensure system integrity, and defend against unauthorized access or cyberattacks.
Q9: What are the three main points of cyber security?
Confidentiality, Integrity, and Availability—known as the CIA Triad.
Q10: What skills are needed for cybersecurity?
Key skills include networking, programming basics, risk analysis, penetration testing, incident response, and problem-solving.
Q11: What are the 5 C’s of cyber security?
- Change
- Compliance
- Cost
- Continuity
- Coverage
Q12: Why is everyone studying cybersecurity?
Cybersecurity is in high demand due to increasing cyberattacks, job security, high salaries, and global career opportunities.
Q13: What are the three importances of cyber security?
It protects privacy, secures financial assets, and maintains trust in digital systems.
Q14: Why is the study about cybersecurity awareness important?
Awareness training helps individuals detect scams, avoid risky behaviors, and strengthen the human element of security.
Q15: Why is cyber security important in everyday life?
It prevents identity theft, financial fraud, and unauthorized access to personal devices and accounts.
Q16: What are some careers that relate to cybersecurity?
Cybersecurity analyst, ethical hacker, SOC analyst, penetration tester, security architect, and forensic investigator.
Q17: How is AI used in cybersecurity?
AI is used for threat detection, anomaly monitoring, automated response, and predicting potential cyber risks.
Q18: What are the 5 essential elements of cyber security?
- Application security
- Information security
- Network security
- End-user education
- Business continuity
Q19: What programming language is needed for cybersecurity?
Python, C/C++, Java, and SQL are commonly used in cybersecurity for analysis and threat detection.
Q20: What’s the easiest role in cybersecurity?
Entry-level roles like IT help desk or SOC analyst are often considered the easiest starting points.
Q21: What are the five types of cyber security?
Network security, Cloud security, Application security, Endpoint security, and IoT security.
Q22: Is cyber security hard?
It can be challenging due to constant learning, but with training and practice, anyone can build a career in cybersecurity.
Q23: What is the best cybersecurity company?
Top companies include Palo Alto Networks, Cisco, CrowdStrike, and Fortinet.
Q24: Who is the most powerful cybersecurity in the world?
The U.S. Cyber Command and companies like Palo Alto Networks are considered global leaders in cybersecurity.
Q25: Who was the first cyber hacker?
Kevin Mitnick is often recognized as one of the first famous hackers.
Q26: Do you need to know coding for cyber security?
Basic coding knowledge is helpful but not mandatory for all roles.
Q27: Is cyber security a stressful job?
Yes, due to high responsibility and constant threat monitoring, but it also offers rewarding challenges.
Q28: Is cybersecurity one word?
Yes, “cybersecurity” is commonly written as one word.
Q29: Can AI replace cybersecurity?
AI can enhance cybersecurity, but human expertise is still essential to handle complex attacks.
Q30: What is cyber crime?
Cybercrime is illegal activity conducted through digital means, such as hacking, identity theft, or online fraud.
Q31: Can AI find bugs in code?
Yes, AI-powered tools can detect coding vulnerabilities faster than traditional methods.
Q32: What is the hardest field in cyber security?
Advanced penetration testing and reverse engineering are among the hardest.
Q33: How many hours does cyber security work a day?
Typically 8–10 hours, but some roles require on-call availability during emergencies.
Q34: What education is needed for cybersecurity?
A degree in computer science, IT, or cybersecurity plus certifications like CEH, CISSP, or CompTIA Security+.
Q35: What is the most important thing in cybersecurity?
Protecting sensitive data and ensuring trust in digital systems.
Q36: How many types of cyber security are there?
Generally 5 to 7 major types, depending on classification.
Q37: What are the 5 benefits of using cyber security?
- Protects data
- Prevents cyberattacks
- Builds trust
- Supports compliance
- Reduces financial risks
Q38: What are common cyber threats?
Phishing, ransomware, malware, denial-of-service attacks, and identity theft.
Q39: How important is cybersecurity in today’s world?
It is critical, as almost every aspect of modern life relies on secure digital systems.
Q40: What is the goal of cyber security training?
To equip individuals and businesses with knowledge to detect, prevent, and respond to cyber threats.
Q41: What are the 3 C’s of cybersecurity?
Cyber awareness, Cyber hygiene, and Cyber resilience.
Q42: Which country is best to study cyber security?
The U.S., U.K., Canada, and Germany are top destinations for cybersecurity education.
Q43: What are the 7 domains of cyber security?
Network, Endpoint, Application, User, Data, Perimeter, and Governance.
Q44: What are five careers in cybersecurity?
- Ethical hacker
- Security analyst
- SOC analyst
- Forensic investigator
- Security engineer
Q45: What is another name for cyber security?
Information security or IT security.
Q46: Why is IT called cyber security?
Because it involves protecting digital systems and networks, often referred to as “cyberspace.”
Q47: Why do people quit cybersecurity?
High stress, workload, and constant learning demands can cause burnout.
Q48: What is a SOC analyst?
A Security Operations Center (SOC) analyst monitors, detects, and responds to security threats in real time.
Q49: Is cyber security a high paying job?
Yes, many roles offer six-figure salaries, especially with experience and certifications.
Q50: What are the four pillars of cybersecurity?
Identify, Protect, Detect, and Respond.
Q51: What are the 6 tips of cyber security awareness?
- Use strong passwords
- Enable 2FA
- Avoid phishing scams
- Update software
- Secure Wi-Fi
- Backup data
Q52: Can a non-IT person learn cyber security?
Yes, many entry-level certifications are designed for beginners without IT backgrounds.
Q53: Who is the famous Pakistani IT expert?
Rafay Baloch is a well-known Pakistani ethical hacker and cybersecurity researcher.
Q54: Who is the #1 hacker in the world?
Kevin Mitnick (now a security consultant) is considered one of the most famous hackers in history.
Q55: Can I make $200,000 a year in cyber security?
Yes, senior roles like Chief Information Security Officer (CISO) can pay over $200K annually.
Q56: How long do hackers go to jail?
Sentences vary, from months to decades, depending on the severity of the crime.
Q57: Which country is the most hacker?
Countries like Russia, China, and North Korea are frequently associated with high levels of hacking activity.
Q58: Is the dark web for hackers?
The dark web is often used by hackers for illegal activities, but it also hosts legitimate privacy-focused communities.
Q59: What is Tor?
Tor (The Onion Router) is software that allows anonymous browsing and access to the dark web.
Q60: Who invented the dark web?
The U.S. Naval Research Laboratory developed the technology behind Tor in the 1990s.
Q61: Why can’t the dark web be shut down?
Because it operates on decentralized, encrypted networks that are difficult to regulate or control.
Conclusion: Your Role in Building a Safer Digital World
In a world where digital and physical realities are merging, learning about cybersecurity is more than a technical skill—it’s a form of personal and professional empowerment. It allows you to take control of your digital life, protecting your financial well-being, personal information, and reputation from a constant barrage of threats. It’s about developing a mindset of vigilance, understanding that a small amount of caution can prevent a major disaster. By adopting simple, proactive habits and sharing your knowledge with others, you become an active participant in building a safer digital environment for everyone. Start today by changing that one-password-for-everything habit, and you’ll be on your way to becoming a savvy and secure digital citizen.