The Vital Role of Critical Infrastructure in Our Daily Lives and the Impact of Disruptions
For this reason, it is of the utmost importance to ensure the protection of these vital systems, in addition to other significant organizations, in order to ensure that society will continue to operate in a manner that is both secure and efficient.
Why Cybersecurity Is Essential: Protecting Individuals and Critical Infrastructure in a Connected World
Because of the interconnected nature of the modern world, it is to everyone’s advantage to have access to solutions that are effective in terms of cybersecurity. A cybersecurity assault can have a number of unpleasant effects on an individual level, including the theft of identity, attempts at extortion, and the loss of critical data such as images of the family. These are just some of the negative outcomes that can occur. These are but a few examples of the harmful consequences that may be brought about. Just a few of the many potential occurrences that could take place are listed here.
Our daily lives rely heavily on critical infrastructure—like hospitals, power plants, and financial institutions. These essential services keep our communities running, and any disruption can have serious consequences. That’s why it’s crucial to protect these vital systems, along with other key organizations, to ensure society continues to operate safely and efficiently.
The Crucial Role of Cyber Threat Research and Scalable Cloud Security in Protecting Our Digital Society
Additionally, the work that is done by cyberthreat researchers, such as the team of 250 threat researchers at talos, who analyze both new and existing threats in addition to cyberattack strategies, is beneficial to everyone. This is because the work that is done by these researchers is beneficial to everyone. Each and every individual will be able to get something from this effort. Furthermore, vulnerabilities that had not been exposed in the past are brought to light, the general public is made more aware of the relevance of cybersecurity, and open-source software instruments are improved. All of these things are accomplished simultaneously. The existing level of protection that is offered to all users of the internet has been greatly raised as a direct result of the work that they have done. There are a vast variety of different kinds of threats that might be encountered in the field of cybersecurity.
-
Cyber threat researchers improving internet security — Talos team analyzes evolving cyber threats to expose vulnerabilities and enhance cybersecurity tools.
-
Cloud security for rapid threat detection and remediation — Advanced cloud security solutions provide better visibility and intelligence to prevent malware attacks.
-
Protecting applications and data in hybrid and remote work environments — Essential cloud security measures safeguard sensitive information and maintain user productivity.
-
Scalable cloud security for growing cloud infrastructure — Ensures comprehensive protection across multiple users, devices, and cloud-hosted applications.
The concept of security in the realm of cloud computing cloud security enables the rapid detection and remediation of threats, as well as the creation of visibility and intelligence, with the goals of preventing the effects of malware. Cloud security also enables the development of visibility and intelligence. The goal behind all these efforts is to strengthen cloud security in a meaningful and effective way. With strong cloud security in place, organizations gain better visibility and deeper insights into their systems—an advantage that can’t be overstated. As more businesses embrace hybrid and remote work models, protecting applications, data, and users has become not just important, but essential.
Additionally, it delivers a streamlined security approach, streamlines security without compromising user productivity, and offers comprehensive protection in scenarios that utilize several cloud services. All of these advantages are absolutely necessary. In addition, it is necessary for the protection of users, which is a necessity that is of the first importance. Scalability in cloud security refers to the degree to which it may be utilized to safeguard an ever-increasing number of users, devices, and applications that are hosted in the cloud. Scalability is a key feature of cloud security. It is generally agreed that scalability is an essential component of cloud security. When this takes place, it guarantees that full coverage is supplied across all potential points of attack, in the event that these points of attack are discovered.
Key Role of Identity Security and Access Management in Cisco’s Multi-Cloud Defense Solutions
Identity security and access management are key pillars of modern information security. Their main role is to protect the digital identities of individuals, devices, and organizations. Whether it’s a person logging into a secure system or a device accessing sensitive data, these tools help ensure that only the right users have the right access—keeping digital environments safe and trustworthy. For the purpose of accomplishing this target, it is required to adopt security procedures, technologies, and policies that restrict user access to accounts and enhance productivity by allowing unrestricted access to vital information without exposing users to any potential danger. This is necessary in order to achieve the goal. For the purpose of providing a more concrete example,
The following are the three key goals that identity security must attempt to achieve:
-
Identity security and access management protect digital identities by ensuring only authorized users and devices can access sensitive resources, enhancing cybersecurity in multi-cloud environments.
-
Monitoring access activity for unusual behavior helps detect potential threats early, allowing organizations to prevent vulnerabilities from being exploited.
For the purpose of achieving the objective of establishing the user’s identification, it is necessary to grant permission to access the resources that are suitable for the purpose. When monitoring access activity, it’s important to watch for unusual behavior or weak security postures that could signal potential threats. Spotting these warning signs early can help you identify vulnerabilities before they’re exploited. Conduct additional study into the capabilities of Cisco Identity Intelligence | Proceed with your investigation and continue your investigation. It is recommended that you proceed with your investigation into the possibilities offered by Continuous Identity Security.
Viruses and other forms of malicious software : A group of software that is meant to either gain illegal access to a computer or to purposefully cause damage to the machine is referred to as “malware.” Both types of software fall under the category of malware, which can be designed to perform a range of harmful actions. To better understand how Secure Endpoint protects against malware threats, check out our other articles. Interested in trying it for yourself? Secure Endpoint also offers a free trial.
Understanding Secure Email Solutions: Protecting Against Phishing and Ransomware Threats
The phishing attempts that are being made at the moment Phishing is a method that involves sending bogus emails that are designed to give the impression that they come from real businesses or organizations. There is a type of social engineering known as phishing. The sending of fake emails is one of the acts that can be classified as belonging to this category. Theft of identity is the most common form of cybercrime, and the major objective of this sort of criminal activity is to acquire sensitive information such as credit card numbers and login information. Theft of identity is also referred to as identity theft sometimes. One such term that might be used to describe them is “phishing.” You can make a substantial contribution to the safety of your personal information by either educating yourself or by employing a technological solution that filters out bogus messages. Both of these options are available to you.
-
Secure Email Solution Free Trial Download – Users can download a free trial version of secure email solutions to protect their inboxes from cyber threats.
-
Phishing Email Attacks and Social Engineering Prevention – Phishing involves fake emails designed to steal sensitive data like credit card numbers and login credentials through social engineering techniques.
-
Identity Theft Protection Through Education and Technology – Educating users and using advanced email filtering technologies can significantly reduce the risk of identity theft from phishing scams.
-
Ransomware Threats and Impact on Data Access – Ransomware blocks access to files or systems demanding payment, but paying ransom does not guarantee data recovery or system restoration.
Here we have the ransomware in question. Within the realm of malicious software, there exists a category that is commonly known as ransomware. Another name for this type of software is “ransomware.” The purpose of this is to extort money from individuals who are vulnerable to being taken advantage of by it. It does this by prohibiting its victims from accessing files or the computer system until the required amount is paid. Even in the case that the ransom is paid, there is no guarantee that the files will be recovered or that the system will be successfully restored. Neither of these conditions can be guaranteed. There is no difference in this aspect, regardless of whether or not the cash is released.
Combating Social Engineering and Enhancing Cybersecurity with Extended Detection and Response (XDR)
Societal control and manipulation carried out by the society the objective of the attackers is to trick you into divulging information that is considered to be confidential by employing a tactic that is known as social engineering. The individuals who were responsible for the attack have the power to either demand a monetary payment or gain access to the private information that you have access to. Any one of these two outcomes is a distinct possibility. It is possible that the combination of social engineering with any of the hazards outlined above could increase the likelihood that you will trust a malicious source, click on links, or download malware.
-
Urgent Need for Swift Action Against Social Engineering Attacks — Immediate measures are essential to stop attackers who manipulate individuals into revealing confidential information or making payments.
-
Social Engineering Amplifies Other Cyber Threats — By exploiting human behavior, social engineering often works alongside malware and phishing, increasing the risk of clicking malicious links or downloading harmful files.
-
XDR Systems Integrate Security Tools for Comprehensive Threat Detection — Extended Detection and Response combines solutions across the entire security stack, improving visibility and enabling faster identification of complex threats.
-
Enhanced Cybersecurity Awareness and Incident Response through XDR — With better data context and unified monitoring, security teams can prioritize responses, reduce attack impacts, and prevent future breaches effectively.
Social engineering often works in combination with other security threats, making it even more dangerous. Because it relies on manipulating human behavior, it can be used alongside various attack methods. To defend against these tactics effectively, it’s important to gather more information and understand how social engineering techniques are carried out. Members of the population who have been identified as having the potential to be at danger
When analysts have access to an efficient extended detection and response (XDR) system that incorporates solutions across the whole security stack, it is much simpler for them to concentrate on comprehensive threat detection, prioritize incident response, and boost productivity.
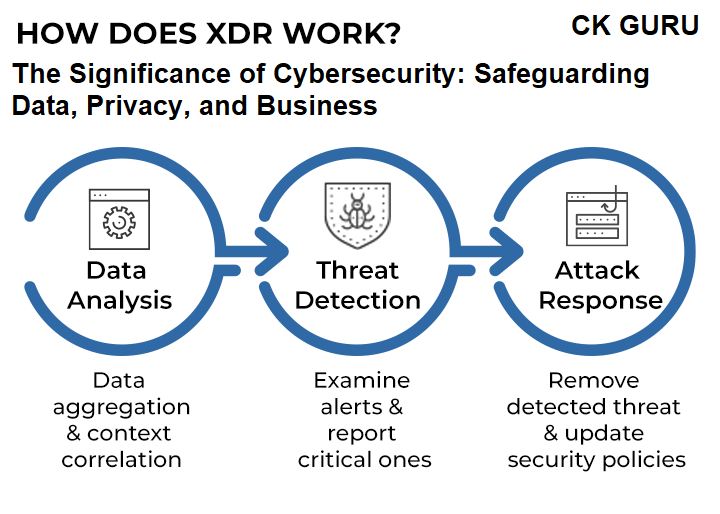
This is because an XDR system brings together solutions that span every layer of the security stack. By integrating tools from across the entire security ecosystem, XDR provides a comprehensive approach to threat detection and response. As a result of enhanced visibility and context into data security problems, events that not only would not have been addressed in the past but will now be brought to a higher degree of awareness will now be brought to the attention of a greater number of people. Implementing this strategy will significantly boost cybersecurity awareness, allowing professionals to detect threats faster and respond more effectively. With increased visibility and timely action, teams can reduce the impact of an attack and prevent future damage.
Enhancing Security with Cisco XDR and Zero-Trust Implementation Strategies
Want to learn more about Cisco XDR and how it enhances your security posture? Click here to explore how it works. Remember, no single tool or technology is completely foolproof—layered security is key to staying protected. This is true for both things and technology. It is important to keep in mind the business operations, risks, and security outcomes of the company when putting this security plan into action during the implementation phase. This is the most effective technique for effective implementation. This is the most efficient method for achieving the desired result. When it comes to the implementation of zero-trust security, the vast majority of companies place a high significance on the adoption of technologies such as multi-factor authentication (MFA), device posture checks, zero trust network access (ZTNA), and network segmentation.
These technologies play a key role in successfully implementing zero-trust security by helping protect sensitive data at every level. While there are multiple paths organizations can take to reach zero-trust maturity, the ultimate goal remains the same: securing access and safeguarding critical information through continuous verification and strict access controls. When it comes to zero-trust networking configurations, there are two places that can provide additional knowledge. For example, Cisco Duo and Cisco Secure Access are included in these resources.
Essential Cybersecurity Best Practices: Updates, Strong Passwords, and Multi-Factor Authentication
By following strong cybersecurity best practices, organizations can greatly reduce the risk of falling victim to cyberattacks. To make these efforts effective, there are three key steps that should always be part of your cybersecurity strategy. One of the most important is keeping both software and operating systems up to date through regular updates and patches.
Regularly updating software and operating systems to the most recent versions helps to increase security measures against future assaults and fixes vulnerabilities that may have been introduced into the system. This is accomplished by maintaining the software and operating systems at their most recent versions. Through the employment of passwords that are not only secure but also one of a kind Because cyberattacks often make use of passwords that are either stolen or not strong enough, the establishment of strong and unique passwords for each online account can be advantageous in boosting cybersecurity.
- Regularly update software and operating systems to fix vulnerabilities and enhance security.
- Use strong, unique passwords for each account to prevent easy access by attackers.
- Implement multi-factor authentication (MFA) for an extra layer of protection against unauthorized access.
- Stay informed about the latest threats and follow cybersecurity standards to proactively protect digital assets.
Cyberattacks often exploit weak or stolen passwords, making them an easy target for attackers. To address this, organizations are increasingly adopting multi-factor authentication (MFA), which adds an extra layer of security to help protect against unauthorized access. Multi-factor authentication demands the fulfillment of a range of different kinds of identification in order to obtain access to an account. This action is taken in order to prevent access by unauthorized individuals. The chance of unauthorized access being gained without authority is decreased as a result of this measure. The Multi-Factor Authentication (MFA) capability is a component of Cisco Duo, and it is able to communicate with the vast majority of applications that are regularly used as well as applications that are significantly more specialized.
Adhering to cybersecurity standards is an important step toward enhancing protection and safeguarding digital assets. To stay ahead of cybercriminals, it’s crucial to remain vigilant and stay informed about the latest threats and security measures. Maintaining a proactive approach is key to understanding and responding to new risks effectively.




